Crack Nt Hash Windows 7 Online
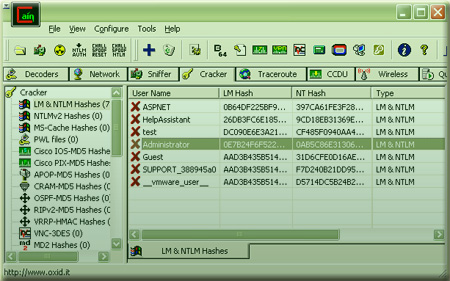
Password hashes:. LM hásh. NT hash.
CrackStation uses massive pre-computed lookup tables to crack password hashes. These tables store a mapping between the hash of a password, and the correct password for that hash. The hash values are indexed so that it is possible to quickly search the database for a given hash. OphCrack is available for free which is a rainbow-table based tool for password cracking on Windows. It is a popular Windows password cracking tool which can also be used on Linux or Mac. It can crack LM and NTLM hashes. For cracking Windows 7, Vista or Windows XP, free rainbow-tables are made available. RainbowCrack Introduction. RainbowCrack is a general propose implementation of Philippe Oechslin's faster time-memory trade-off technique. It crack hashes with rainbow tables. RainbowCrack uses time-memory tradeoff algorithm to crack hashes. It differs from brute force hash crackers.
cachéd-credentials hash ( fór offline authéntication)PtH can just take advantage of the initial two, as the 3rd has sodium with it.for area accounts, LM hash NT hash can be found in memory space when user logons (interactive Iogon, eg, logon type 2 or 10) member host, it goes away when user logoff, while the cached credential will end up being kept to storage for that consumer authentication offline next period. ( by default, windóws save 10 cached hashes in registry)while making use of logon kind 3 ( system logon), No hash will be can be found on the member machine ( storage or drive). Have got you ever produced a link to a potentially compromised remote machine making use of a fortunate domain account and wondered if there was any chance that your happy credentials could become exposed in some method to the attacker? After thinking and stressing about it, the attention (and paranoia) lastly obtained to me and therefore I fixed off on a journey to study attacks against domain credentials, and in specific, their implication for occurrence responders. I've shown on this topic a few situations and today I will (lastly) consider the time to record my findings.
This is definitely the 1st post in what will be a multi-part collection on this research.I find this to end up being a exciting topic and one which should become of attention to the whole IR community. That stated, be forewarned that these content will not really be fast scans. If you'll stick with me even though, I believe it will become worth your time because you should stroll away understanding specifically what you cán and cannot perform properly with your privileged domain balances.So right here we move! The ScenarioLet's begin with a scénario-a worst case, yet realistic scenario-where we possess a Home windows XP Services Group 2 client device on our website that is most likely compromised. We need to analyze it to evaluate harm, but it must stay online.The cause I call this a “worst case” situation is certainly that XP SP2 provides numerous vulnerabilities which create it fairly simple for an attacker to gain administrative liberties (in reality SYSTEM-level liberties) on the sponsor, thereby enabling malware to proceed after your credentials with complete system power. The reason for calling it “realistic” is that many organizations nevertheless possess XP techniques on their network and there are almost usually a small number of systems that fail to obtain patched properly for one reason or another.Today in order to assess and triage this potentially compromised device, we need the capability to do various tasks:.
Query the device, with a device such as WMIC:There are usually plenty of issues we might would like to question from the program, such as working processes, installed solutions, logged on users, patch ranges, etc. Fortunately we have a great device like WMIC to assist us with this task. For even more on WMIC, check out out from Ed Skoudis concerning this tool. Run processes on the machine, with a tool like PsExec:PsExec is a Microsoft Sysinternals tool that provides a extremely effective method to operate tools on a remote device. For this reason, it's quite well-known in our line of function and therefore I need to create sure to cover it.
That mentioned, it's important for me to point out that you should generally avoid PsExec with alternative qualifications, in which you designate the “-u” choice to the control. I'll discuss the alternative credentials dangers later on in this article, as well as a follow-up write-up devoted to PsExec. Duplicate data files to from the machine, via the command NET Make use of:Finally, we require a way to move files on and off the target system, therefore why not really map a push to the remote control machine with Internet USE?The RequirementsIn purchase to do effective IR, we must possess administrative accessibility to the compromised device. Without it, we will almost certainly skip essential indications of disease.